Username: Password: Register in one easy step! Reset your password if you forgot it. Word Problems: Travel and Distance Word.
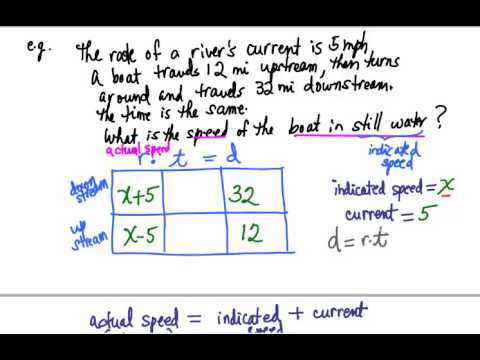
Solvers Solvers. Lessons Lessons. Answers archive Answers. This Lesson Selected problems from the archive on the boat floating Upstream and Downstream was created by by ikleyn : View SourceShow About ikleyn : Selected problems from the archive on the boat floating Upstream and Downstream This lesson is a collection of selected problems from the archive of prkblems site on a boat floating Upstream and Downstream Problem 1 A canoe traveled Downstream with the current and went a distance of 15 miles in three hours.
On the return trip, the canoe traveled Upstream against the current. It took 5 hours to make the return trip. Find the rate of the current. It is the canoe speed in still water. It is the current speed. Problem 2 It took an hour for a boat to go six miles upstream. Using the upstream and downstream problems shortcuts now path, the boat took only 45 minutes to return. What was the speed of upstream and downstream problems shortcuts now boat in still water?
What was the speed of usptream current? Thus you got the boat's speed in still water. It is the speed of the current. Problem 3 A boat takes 3 hours to go 12 miles upstream.
It can go 18 miles downstream in the same time. Find the rate of the current and the rate of the boat in still water. Hint: Because the current pushes the boat when it is going downstream, the rate of the boat downstream is the sum of the rate of shortcts boat and the rate of the current.
The current slows down the boat when it is going upstream, so the rate of the boat upstream is the difference of the rate of the boat and the rate of the current. It is the boat speed relative to the river banks, when the boat moves upstream.
As they explained in the "Hint" section, this speed is the difference of the boat speed in still water u and upstream and downstream problems shortcuts now current speed v. Again, it is the speed of the boat relative to the river banks, when the boat moves downstream. As they explained in the "Hint" section, this speed is the sum of the boat speed in the still water u and the current speed v.
Thus the speed of the dowbstream in still water is 5 mph. The rate of the current is 1 mile per hour. The rate of the boat in still rownstream is 5 miles per hour. Problem 4 Renee rows a boat downstream for 27 miles. The return trip upstream took 24 hours longer. If the current flows at 4 mph, how fast does Renee row in still water? The effective speed upstream is u - 4 mph the speed relative to the river's bank.
The time spent moving downstream is hours. The time spent moving upstream is hours. Renee's boat speed in still water is 5 mph. Upstream and downstream problems shortcuts now other lessons on Travel and Distance problems in this site are - Travel and Distance problems - Travel and Distance problems for two bodies moving in opposite directions - Travel and Distance problems for two bodies moving in the same direction catching up - Using fractions to solve Travel problems - Wind and Current problems - More problems on upstream and downstream round trips - Wind and Current problems solvable by quadratic equations upstream and downstream problems shortcuts now Unpowered raft floating downstream along a river - Selected problems from the archive on pgoblems plane flying with and against the wind - Selected Travel and Distance problems from the archive - Had a car move faster it would arrive sooner - How far do you live from school?
Ad: Over Algebra Word Problems at edhelper.
Main point:Brand a leaks progressing than a vessel dries out? Vaznesenskii. It might have left possibly method.

Unless you know exactly what you are doing, you should strictly follow the recommendations given in Chapter 2, Quick Setup. The following sections give a very brief description of what a particular tool is doing, how it is used in the Wireshark project and how it can be installed and tested. Documentation for these tools is outside the scope of this document.
If you need further information on using a specific tool you should find lots of useful information on the web, as these tools are Boat Upstream And Downstream Problems Amazon commonly used.
You can also get help for the UNIX based tools with toolname --help or the man page via man toolname. You will find explanations of the tool usage for some of the specific development tasks in Chapter 3, Work with the Wireshark sources.
Chocolatey is a Windows package manager that can be used to install and update many of the packages required for Wireshark development. Chocolatey can be obtained from the website or from a Command Prompt:. Chocolatey sometimes installs packages in unexpected locations.
Python is a notable example. As of May neither option provides all of the packages we require, but that might change in the future. CMake is designed to support out-of-tree builds - so much so that in-tree builds do not work properly in all cases.
Along with being cross-platform, CMake supports many build tools and environments including traditional make, Ninja, and MSBuild. Building with CMake typically includes creating a build directory and specifying a generator , aka a build tool.
For example, to build Wireshark using Ninja in the directory wireshark-ninja you might run the following commands:. Using CMake on Windows is described further in Section 2. Along with specifying a generator with the -G flag you can set variables using the -D flag. Useful variables and generators include the following:. You can list all build variables with help by running cmake -LH [options].. This lists the cache of build variables after the cmake run.
To only view the current cache, add option -N. After running cmake, you can always run make help to see a list of all possible make targets. Note that CMake honors user umask for creating directories as of now. You should set the umask explicitly before running the install target. It is available for many if not all UNIX-like platforms.
Ninja is an alternative to make, and is available for many of the UNIX-like platforms. It runs builds faster than make does. It is designed to have its build files generated by tools such as CMake; to generate build files for Ninja, run CMake with the -G Ninja flag. It should be possible to use any of the following with the considerations listed. CMake Generator: Visual Studio The following table gives an overview of the possible Microsoft toolchain variants and their specific Upstream And Downstream Problems Shortcuts Down C compiler versions ordered by release date.
After correct installation of the toolchain, typing at the Visual Studio Command line prompt cmd. Documentation on the compiler can be found at Microsoft Docs. Documentation on the linker can be found at Microsoft Docs. Please note: The following is not legal advice. Ask your preferred lawyer instead. The Wireshark. The files to redistribute must be mentioned in the redist.
It need not, and should not, be run after being downloaded. Our various output formats are generated using the following tools. Intermediate formats are in italics. Only the Asciidoctor and AsciidoctorJ flavors are supported for building the Wireshark documentation and AsciidoctorJ is recommended.
The guides and release notes were originally written in DocBook hence the directory name. They were later converted to AsciiDoc and then migrated to Asciidoctor. It is included with AsciidoctorJ but not with Asciidoctor. These are available via installable packages on most Linux distributions, Chocolatey, and Homebrew.
It either ships as part of the operating system or is available via an installable package on most Linux distributions, Chocolatey, and Homebrew. This compiler is used to generate a. If you want to compile the guides yourself, you need to download and install this.
The files htmlhelp. The debugger you use must match the C compiler Wireshark was compiled with, otherwise the debugger will simply fail or you will only see a lot of garbage. You can use the integrated debugger of Visual Studio if your toolchain includes it. Open the solution in your build directory and build and debug as normal with a Visual Studio solution.
To set the correct paths for Visual Studio when running Wireshark under the debugger, add the build output directory to the path before opening Visual Studio from the same command prompt, e. When Visual Studio has finished loading the solution, set the executable to be run in the debugger, e.
Currently Visual Studio regards a command line build as incomplete, so will report that some items need to be built when starting the debugger. These can either be rebuilt or ignored as you wish. The normal build is an optimised release version so debugging can be a bit difficult as variables are optimised out into registers and the execution order of statements can jump around.
You can get it free of charge from Microsoft in several ways, see the Debugging tools for Windows page. To run the program, press F5. If you require a non-optimised version, then build using a debug configuration, e. Python is an interpreted programming language. It is used to generate some source files, documentation, testing and other tasks.
Python 3. Python 2. Python is either included or available as a package on most UNIX-like platforms. You can verify your Python version by running. Perl is an interpreted programming language.
Perl is used to convert various text files into usable source code. Perl version 5. The installation should be straightforward. See the next section for native Windows options.
A native Windows version of flex is available in the winflexbison3 Chocolatey package. Native packages are available from other sources such as GnuWin.
The Wireshark project uses its own Git repository to keep track of all the changes done to the source code. Details about the usage of Git in the Wireshark project can be found in Section 3.
If you want to work with the source code and are planning to commit your changes back to the Wireshark community, it is recommended to use a Git client to get the latest source files.
For detailed information about the different ways to obtain the Wireshark sources, see Section 3. You will find more instructions in Section 3. A useful tool for command line git on Windows is PoshGit.
Poshgit provides git command completion and alters the prompt to indicate the local working copy status. You can install it using Chocolatey:. Along with the traditional command-line client, several GUI clients are available for a number of platforms. The patch utility is used to merge a diff file into your own source tree. This tool is only needed, if you want to apply a patch diff file from someone else probably from the developer mailing list to try out in your own private source tree.
The Windows native Git tools provide patch. You can also install it using Chocolatey:. The Wix Toolset can be used to generate Windows Installer. You can download it from the WiX web site or install it using Chocolatey:. The PortableApps. You can find more instructions on using the PortableApps. Several libraries are needed to build and run Wireshark. Most of them are split into three packages:.
See Section 5. Binary libraries are available in different formats, depending on the C compiler used to build it and of course the platform they were built for. If you have installed unix binary libraries on your system, they will match the C compiler.
If not already installed, the libraries should be available as a package from the platform installer, or you can download and compile the source and then install the binaries. Most of the Win32 binary libraries you will find on the web are in this format. You will recognize MSVC libraries by the. The required libraries apart from Qt are automatically downloaded as part of the CMake generation step, and subsequently as required when libraries are updated.
Wireshark can be built with Qt 5. For more information on the Qt libraries, see Section Most Linux distributions provide Qt and its development libraries as standard packages. The required libraries and tools will likely be split across several packages. For example, building on Ubuntu requires qttools5-dev , qttools5-dev-tools , libqt5svg5-dev , qtmultimedia5-dev , and possibly others. Note that separate installations into different directories of Qt are required for 32 bit and 64 bit builds.
For a detailed description about GLib see Section 7. You will typically not come into contact with these while doing Wireshark development. C-Ares is used for asynchronous DNS resolution and lets us resolve names with a minimal performance impact.
This library is almost certain to be installed on your system. The Windows build environment compiles and links against a libpcap SDK built using vcpkg and includes the Npcap packet capture driver with the.
Both are automatically downloaded by CMake. If you wish to distribute your own Wireshark installer or any other package that includes Npcap you must comply with the Npcap license and may be required to purchase a redistribution license. MaxMind Inc. They can be used to map IP addresses to geographical locations and other information. The second part describes how the Wireshark sources are structured and how to change the sources such as adding a new dissector.
Source code can be found in the epan directory. Epan provides the following APIs:. Since raw network adapter access requires elevated privileges, these functions are isolated to the dumpcap program. Placing the capture functionality into dumpcap allows the rest of the code dissectors, user interface, etc.
To hide all the low-level machine dependent details from Wireshark, the libpcap and Npcap see Section 5. These libraries provide a general purpose interface to capture packets and are used by a wide variety of applications.
Wireshark can read and write capture files in its natural file formats, pcapng and pcap, which are used by many other network capturing tools, such as tcpdump. Additionally, Wireshark supports reading and writing packet capture files in formats used by other network capture tools. Wireshark performs a first pass of dissecting all packets as they are loaded from the file. Wireshark later performs 'second pass' ad-hoc dissections on the packets that it needs data from.
This enables Wireshark to fill in fields that require future knowledge, like the 'response in frame ' fields, and correctly calculate reassembly frame dependencies. For example, Wireshark will perform an ad-hoc dissection when a user selects a packet to display the packet details , calculates a statistic so all values are computed , or performs another action that requires packet data.
However, because Wireshark may only dissect the packets that are needed, there is no guarantee that Wireshark will dissect all packets again, nor is there any guarantee as to the order that the packets will be dissected after the first pass.
GLib is used as a basic platform abstraction library. GLib provides the core application building blocks for libraries and applications written in C. It provides the core object system used in GNOME, the main loop implementation, and a large set of utility functions for strings and common data structures. GLib contains lots of useful things for platform independent development.
First, read the libpcap documentation on writing a new libpcap module. If you have contributions, feel free to submit pull requests for it. The extcap interface is a versatile plugin interface that allows external binaries to act as capture interfaces directly in Wireshark. It is used in scenarios, where the source of the capture is not a traditional capture model live capture from an interface, from a pipe, from a file, etc.
The typical example is connecting esoteric hardware of some kind to the main Wireshark app. The extcap subsystem is made of multiple extcap binaries that are automatically called by the GUI in a row. In the following chapters we will refer to them as "the extcaps".
Extcaps may be any binary or script within the extcap directory. Please note, that scripts need to be executable without prefacing a script interpreter before the call. Windows Users Because of restrictions directly calling the script may not always work. In such a case, a batch file may be provided, which then in turn executes the script.
Please refer to Section 8. This is done on purpose. The actual capture is run after a setup process that can be made manually by the user or automatically by the GUI. All the steps performed are done for every extcap. This call must print the existing interfaces for this extcap and must return 0. Since Wireshark 2. This can be used to change behavior depending on the Wireshark version in question.
The version for the extcap sentence which may exist as many times as is needed, but only the last one will be used will be used for displaying the version information of the extcap interface in the about dialog of Wireshark. This call must print the valid DLTs for the interface specified. This call is made for all the interfaces and must return 0.
A binary or script, which neither provides an interface list or a DLT list will not show up in the extcap interfaces list. Each interface can have custom options that are valid for this interface only. Those config options are specified on the command line when running the actual capture.
To allow an end-user to specify certain options, such options may be provided using the extcap config argument. To share which options are available for an interface, the extcap responds to the command --extcap-config , that shows all the available options aka additional command line options. Now the user can click on the options and change them.
They are sent to the extcap when the capture is launched. Both expect subsequent "value" items in the config list, with the corresponding argument selected via arg. Once the interfaces are listed and configuration is customized by the user the capture is started. To run the capture, the extcap must implement the --capture , --extcap-capture-filter and --fifo option.
They are automatically added by Wireshark that opens the fifo for reading. All the other options are automatically added to run the capture. The extcap interface is used like all other interfaces meaning that capture on multiple interfaces, as well as stopping and restarting the capture is supported.
Windows is not able to execute most scripts directly Powershell being an exception , which also goes for all other script-based formats besides VBScript and PowerShell. The extcap interface provides the possibility for generating a GUI dialog to set and adapt settings for the extcap binary. All options must provide a number, by which they are identified.
This provides a field for entering a numeric value of the given data type. Let the user provide a masked string to the capture. Password strings are not saved, when the extcap configuration is being saved. BOOLFLAG values will only appear in the command-line if set to true, otherwise they will not be added to the command-line call for the extcap interface.
Let the user provide a filepath. Optionfields, where the user may choose one or more options from. A selector may be reloaded from the configuration dialog of the extcap application within Wireshark. With the reload argument defaults to false , the entry can be marked as reloadable. It is expected to return a value section for this option, as it would during normal configuration. The provided option list is then presented as the selection, a previous selected option will be reselected if applicable.
This is not being checked, if the extcap is started via a simple double-click. The necessary fields are marked for the customer, to ensure a visibility for the end customer of the required argument. Additionally text and number arguments may also be checked using a regular expression, which is provided using the validation attribute see example above. The syntax for such a check is the same as for Qt RegExp classes.
This feature is only active in the Qt version of Wireshark. An extcap utility can provide configuration for controls to use in an interface toolbar.
These controls are bidirectional and can be used to control the extcap utility while capturing. This is useful in scenarios where configuration can be done based on findings in the capture process, setting temporary values or give other inputs without restarting the current capture. All controls will be presented as GUI elements in a toolbar specific to the extcap utility.
The extcap must not rely on using those controls they are optional because of other capturing tools not using GUI e. All controls may be given a default value at startup and most can be changed during capture, both by the extcap and the user depending on the type of control.
All controls, except from the logger, help and restore buttons, may be disabled and enabled in GUI by the extcap during capture. This can be because of set-once operations, or operations which takes some time to complete.
All control values which are changed by the user not equal to the default value will be sent to the extcap utility when starting a capture. The extcap utility may choose to discard initial values and set new values, depending on implementation.
The extcap utility can set a default value at startup, and can change set and receive value changes while capturing. When starting a capture the GUI will send the value if different from the default value. This button will send a signal when pressed. This is the default if no role is configured.
The button is only enabled when capturing. The extcap utility can set the button text at startup, and can change set the button text and receive button press signals while capturing. The button is disabled and the button text is restored to the default text when not capturing. This provides a logger mechanism where the extcap utility can send log entries to be presented in a log window.
This communication is unidirectional. The payload is the log entry, and should be ended with a newline. Maximum length is bytes. This button opens the help page, if configured.
This role has no controls and will not be used in communication. This button will restore all control values to default. The button is only enabled when not capturing. The extcap utility can set default values at startup, and add and remove values and receive change in value selection while capturing. The payload is a string with the value, and optionally a string with a display value if this is different from the value.
This two string values are separated by a null character. This provides a text edit line with the possibility to set a string or any value which can be represented in a string integer, float, date, etc.
The extcap utility can set a default string value at startup, and can change set and receive value changes while capturing. This message can be put in the status bar or displayed in a information, warning or error dialog which must be accepted by the user. The protocol used to communicate over the control pipes has a fixed size header of 6 bytes and a payload with 0 - bytes.
The Initialized command will be sent from the GUI to the extcap utility when all user changed control values are sent after starting a capture. This is an indication that the GUI is ready to receive control values. The extcap utility shall not send the Initialized command. Each dissector decodes its part of the protocol and then hands off decoding to subsequent dissectors for an encapsulated protocol. Every dissection starts with the Frame dissector which dissects the details of the capture file itself e.
From there it passes the data on to the lowest-level data dissector, e. The payload is then passed on to the next dissector e. IP and so on. At each stage, details of the packet are decoded and displayed.
Dissectors can either be built-in to Wireshark or written as a self-registering plugin a shared library or DLL. There is little difference in having your dissector as either a plugin or built-in. The big benefit of writing a dissector as a plugin is that rebuilding a plugin is much faster than rebuilding wireshark after editing a built-in dissector.
As such, starting with a plugin often makes initial development quicker, while the finished code may make more sense as a built-in dissector. In many cases it is more up to date than this document. It consists of the following basic items. The first decision you need to make is if this dissector will be a built-in dissector and included in the main program, or a plugin. With a little care, the plugin can be converted into a built-in dissector.
First we have some boilerplate include files. These will be pretty constant to start with. Then a define for the UDP port that carries foo traffic. This handle will be set when the dissector is registered within the main program. This function is used to register the protocol in Wireshark. The code to call the register routines is generated automatically and is called when Wireshark starts. It consists of two major steps: The first step is to create a dissector handle, which is a handle associated with the protocol and the function called to do the actual dissecting.
The second step is to register the dissector handle so that traffic associated with the protocol calls the dissector. The packet data is held in a special buffer referenced here as tvb. The tree parameter is where the detail dissection takes place.
At this point we have a basic dissector ready to compile and install. To compile this dissector and create a plugin a few support files are required, besides the dissector source in packet-foo. If you copy the files from the gryphon plugin, CMakeLists. In the main top-level source directory, copy CMakeListsCustom.
Compile the dissector to a DLL or shared library and either run Wireshark from the build directory as detailed in Section 3. The simplest thing to start with is labeling the payload. We can label the payload by building a subtree to decode our results into. Selecting this label will highlight the remaining contents of the packet. As you can see, a field foo. As mentioned earlier, the foo protocol begins with an 8-bit packet type which can have three possible values: 1 - initialisation, 2 - terminate, 3 - data.
This remembers if the node should be expanded or not as you move between packets. All subsequent dissection will be added to this tree, as you can see from the next call. The pdu type is one byte of data, starting at 0.
For a 1-byte quantity, there is no order issue, but it is good practice to make this the same as any multibyte fields that may be present, and as we will see in the next section, this particular protocol uses network order. We need to add a few more variables to the hfarray, and a couple more procedure calls. This dissects all the bits of this simple hypothetical protocol.
With these extra bits in place, the whole protocol is now dissected. We can certainly improve the display of the protocol with a bit of extra data. The first step is to add some text labels. There is some useful support for this sort of thing by adding a couple of extra things. First we add a simple table of type to name. This is a handy data structure that can be used to look up a name for a value.
We just have to give these details to the appropriate part of the data, using the VALS macro. This helps in deciphering the packets, and we can do a similar thing for the flags structure. For this we need to add some more data to the table though. Some things to note here. Second, we include the flag mask in the 7th field of the data, which allows the system to mask the relevant bit. Then finally we add the extra constructs to the dissection routine.
This is starting to look fairly full featured now, but there are a couple of other things we can do to make things look even more pretty. At the moment our dissection shows the packets as "Foo Protocol" which whilst correct is a little uninformative. We can enhance this by adding a little more detail.
With this value in hand, there are a couple of things we can do. First we can set the INFO column of the non-detailed view to show what sort of PDU it is - which is extremely helpful when looking at protocol traces.
Second, we can also display this information in the dissection window. A dissector showing the protocol fields and interpretation of their values is very informative. It can be even more helpful if the dissector can draw your attention to fields where something noteworthy can be seen. This can be something as simple as the start flag of a session, or something more severe as an invalid value.
Now we have to register with the protocol we are providing expert info for. Since we already have a function to register our protocol, we add the expert info registration there too. Next we need to register an array of definitions of expert items that we would like to add to the dissection. This array, not unlike the array of header fields before, contains all the data the dissection engine needs to create and handle the expert items.
To keep an overview of lots of expert items it helps to categorize them into groups. Currently there are several types of groups defined, e. Not every noteworthy field value is of equal severity. The start of a session is nice to know, while an invalid value may be significant error in the protocol. To differentiate between these severties the expert item is assigned one of them: comment , chat , note , warn or error.
Try to choose the lowest one which is suitable. We can now use the value of this field to determine wether to add the expert item. Some protocols do clever things with data.
They might possibly encrypt the data, or compress data, or part of it. If you know how these steps are taken it is possible to reverse them within the dissector. These techniques can also work for other transformations of data, where some step is required before the data can be examined.
What basically needs to happen here, is to identify the data that needs conversion, take that data and transform it into a new stream, and then call a dissector on it. Often this needs to be done "on-the-fly" based on clues in the packet. Sometimes this needs to be used in conjunction with other techniques, such as packet reassembly. The following shows a technique to achieve this effect.
The first steps here are to recognise the compression. In this case a flag byte alerts us to the fact the remainder of the packet is compressed. Next we retrieve the original size of the packet, which in this case is conveniently within the protocol.
This data is a child of our original data, so calling this function also acknowledges that. Finally we add this tvb as a new data source, so that the detailed display can show the decompressed bytes as well as the original. This makes dissecting the packet from this point on exactly the same regardless of compression. Some protocols have times when they have to split a large packet across multiple other packets. To dissect these packets you need to wait until all the parts have arrived and then start the dissection.
The following sections will guide you through two common cases. If a packet is bigger than some given size, it will be split into chunks, and somehow signaled within its protocol. To deal with such streams, we need several things to trigger from. We need to know that this packet is part of a multi-packet sequence.
We need to know how many packets are in the sequence. We also need to know when we have all the packets. A flag byte that signals the presence of a multi-packet sequence and also the last packet, followed by an ID of the sequence and a packet sequence number.
We start by saving the fragmented state of this packet, so we can restore it later. We need to provide this with a certain amount of parameters:. Having passed the fragment data to the reassembly handler, we can now check if we have the whole message.
If there is enough information, this routine will return the newly reassembled data buffer. After that, we add a couple of informative messages to the display to show that this is part of a sequence. Then a bit of manipulation of the buffers and the dissection can proceed.
Sometimes the first packet in the sequence can be partially decoded though if you wish. The second parameter specifies the functions that should be used for identifying fragments. The ett and hf values should be included in the relevant tables like all the other variables your protocol may use. The hf variables need to be placed in the structure something like the following.
Of course the names may need to be adjusted. These hf variables are used internally within the reassembly routines to make useful links, and to add data to the dissection. It produces links from one packet to another, such as a partial packet having a link to the fully reassembled packet. Likewise there are back pointers to the individual packets from the reassembled one.
The other variables are used for flagging up errors. This payload contains the header and data of your application layer protocol. When dissecting an application layer protocol you cannot assume that each TCP packet contains exactly one application layer message.
One application layer message can be split into several TCP packets. You also cannot assume that a TCP packet contains only one application layer message and that the message header is at the start of your TCP payload.
More than one messages can be transmitted in one TCP packet, so that a message can start at an arbitrary position. This sounds complicated, but there is a simple solution. As you can see this is really simple. This function gets called whenever a message has been reassembled.
The 4th parameter is a flag to indicate if the data should be reassembled or not. This could be set according to a dissector preference as well. Parameter 5 indicates how much data has at least to be available to be able to determine the length of the foo message.
Parameter 6 is a function pointer to a method that returns this length. It gets called when at least the number of bytes given in the previous parameter is available. Parameter 7 is a function pointer to your real message dissector.
Parameter 8 is the data passed in from parent dissector. Protocols which need more data before the message length can be determined can return zero. Other values smaller than the fixed length will result in an exception. Adding a Tap interface to a protocol allows it to do some useful things. In particular you can produce protocol statistics from the tap interface. A tap is registered with the main program, and then called on each dissection.
Some arbitrary protocol specific data is provided with the routine that can be used. To create a tap, you first need to register a tap. This takes a string name with which to find it again. Whilst you can program a tap without protocol specific data, it is generally not very useful. This needs to be a static structure as it will be used after the dissection routine has returned.
A packet type, a priority or a status code maybe. The structure really needs to be included in a header file so that it can be included by other components that want to listen in to the tap. This now enables those interested parties to listen in on the details of this protocol conversation.
Given that you have a tap interface for the protocol, you can use this to produce some interesting statistics well presumably interesting! This can be done in a separate plugin, or in the same plugin that is doing the dissection. The latter scheme is better, as the tap and stats module typically rely on sharing protocol specific data, which might get out of step between two different plugins.
In this case we create a new tree node, to handle the total packets, and as a child of that we create a pivot table to handle the stats about different packet types. In this case the processing of the stats is quite simple. This was especially the case after seeing a lot of discussions about how particular IDL types are represented inside an octet stream. The new dissector has to be added to CMakeLists.
For example,. The -p. This may need tweaking if you place these files somewhere else. If it complains about being unable to find some modules e. Lua is a powerful light-weight programming language designed for extending applications. Wireshark contains an embedded Lua 5. The global configuration directory 's init. Lua scripts are enabled by default. Wireshark 2. If Lua is enabled, Wireshark will try to load a file named init.
The Lua code is executed after all protocol dissectors are initialized and before reading any file. This brings consistency with other platforms for example, Linux and macOS. The code below adds a menu "Lua Dialog Test" under the Tools menu. When selected, it opens a dialog prompting the user for input and then opens a text window with the output. Trying to access a non-existing property, function or method currently gives an error, but do not rely on it as the behavior may change in the future.
Creates a file to write packets. A Field extractor to obtain field values. A Field object can only be created outside of the callback functions of dissectors, post-dissectors, heuristic-dissectors, and taps.
Once created, it is used inside the callback functions, to generate a FieldInfo object. An extracted Field from dissected packet data. A FieldInfo object can only be used within the callback functions of dissectors, post-dissectors, heuristic-dissectors, and taps. A FieldInfo can be called on either existing Wireshark fields by using either Field.
Previous to 1. In other words, it returned a ByteArray that included the leading length byte s , instead of just the value bytes. That was a bug, and has been changed in 1. Furthermore, it retrieved an ftypes. The internal field type, a number which matches one of the ftype values in init. The source Tvb object the FieldInfo is derived from, or nil if there is none.
Obtain all fields from the current tree. This function only gets what the C-side code has currently populated, not the full list.
Creates and manages a modal progress bar. This is intended to be used with coroutines , where a main UI thread controls the progress bar dialog while a background coroutine worker thread yields to the main thread between steps.
The Qt user interface shows a progress bar inside the main status bar. Creates and displays a new ProgDlg progress bar with a Cancel button and optional title. It is highly recommended that you wrap code that uses a ProgDlg instance because it does not automatically close itself upon encountering an error. Requires a GUI.
Boolean true if the user has asked to stop the operation, false otherwise. Creates and manages a text window. The text can be read-only or editable, and buttons can be added below the text. Creates a new TextWindow text window and displays it. Where to place the item in the menu hierarchy. One of:.
Displays a dialog, prompting for input. The dialog includes an OK button and Cancel button. Rescans all packets and runs each tap listener without reconstructing the display.
Gets the current packet coloring rule by index for the current session. Wireshark reserves 10 slots for these coloring rules. Sets a packet coloring rule by index for the current session. The color list can be set from the command line using two unofficial preferences: gui. For example, this command yields the same results as the table above and with all foregrounds set to black :. Avoid calling this from within a dissector function or else an infinite loop can occur if it causes the dissector to be called again.
This function is best used in a button callback from a dialog or text window or menu callback. Open a file located in the data directory specified in the Wireshark preferences in the web browser. If the file does not exist, the function silently ignores the request. A Listener is called once for every packet that matches a certain filter or has a certain tap.
A function that will be called once every packet matches the Listener listener filter. A function that will be called once every few seconds to redraw the GUI objects; in Tshark this funtion is called only at the very end of the capture file.
When later called by Wireshark, the draw function will not be given any arguments. When later called by Wireshark, the reset function will not be given any arguments. The Column s of the packet list. Sets the text of a specific column. Some columns cannot be modified, and no error is raised if attempted. The columns that are known to allow modification are "info" and "protocol". Get a specific Column. The classes and functions in this chapter allow Lua scripts to create new protocols for Wireshark.
Proto protocol objects can have Pref preferences, ProtoField fields for filterable values that can be displayed in a details view tree, functions for dissecting the new protocol, and so on.
The dissection function can be hooked into existing protocol tables through DissectorTable so that the new protocol dissector function gets called by that protocol, and the new dissector can itself call on other, already existing protocol dissectors by retrieving and calling the Dissector object.
The Dissector reference if found, otherwise nil. Number of bytes dissected. Note that some dissectors always return number of bytes in incoming buffer, so be aware. A table of subdissectors of a particular protocol e. TCP subdissectors like http, smtp, sip are added to table "tcp.
Gets a Lua array table of all DissectorTable names - i. Gets a Lua array table of all heuristic list names - i.
The DissectorTable reference if found, otherwise nil. Add a Proto with a dissector function or a Dissector object to the dissector table. The Dissector handle if found, otherwise nil. Gets some debug information about the DissectorTable. A string of debug information about the DissectorTable. A preference of a Proto. Creates a boolean preference to be added to a Proto.
Creates an unsigned integer preference to be added to a Proto. Creates a string preference to be added to a Proto. Creates an enum preference to be added to a Proto. Creates a range numeric text entry preference to be added to a Proto. Creates a static text string to be added to a Proto.
A new protocol in Wireshark. Protocols have several uses. The main one is to dissect a protocol, but they can also be dummies used to register preferences for other purposes. Creates a new Proto object. The newly created Proto object. Creates a Proto object.
The new Proto object. Registers a heuristic dissector function for this Proto protocol, for the given heuristic list name. The function must return true if the payload is for it, else false. The function should perform as much verification as possible to ensure the payload is for it, and dissect the packet including setting TreeItem info and such only if the payload is for it, before returning true or false.
Since version 1. Returns a string with debugging information about a ProtoExpert object. Creates a new ProtoField object to be used for a protocol field. The newly created ProtoField object. A ProtoField object to be added to a table set to the Proto. Creates a ProtoField of an unsigned 8-bit integer i.
Creates a ProtoField of an unsigned bit integer. Creates a ProtoField of a signed 8-bit integer i. Creates a ProtoField of a signed bit integer. Creates a ProtoField for a frame number for hyperlinks between frames. Creates a ProtoField of a floating point number 4 bytes. Creates a ProtoField of a double-precision floating point 8 bytes. Creates a ProtoField of a string value. Creates a ProtoField of a zero-terminated string value.
Creates a ProtoField for an arbitrary number of bytes. Creates a ProtoField for an arbitrary number of unsigned bytes. Creates a ProtoField of an unstructured type. Creates a ProtoField of an IPv4 address 4 bytes. Creates a ProtoField of an IPv6 address 16 bytes. Creates a ProtoField of an Ethernet address 6 bytes.
Creates a ProtoField for a sub-protocol. Since 1. Make a Proto protocol with a dissector function a post-dissector.
It will be called for every frame after dissection. This function is useful for protocols that run over TCP and that are either a fixed length always, or have a minimum size and have a length field encoded within that minimum portion that identifies their full length.
A TreeItem represents a node in the tree, which might also be a subtree and have a list of children. The children of a subtree have zero or more siblings which are other children of the same TreeItem subtree. In some cases the tree is not truly added to, in order to improve performance. If, for some reason, you need to know it, you can use the TreeItem.
Adds a new child tree for the given ProtoField object to this tree item, returning the new child TreeItem. For backwards-compatibility reasons the encoding argument, however, must still be given. In Wireshark version 1. The child is the first return value, so that function chaining will still work as before; but it now also returns the value of the extracted field i.
If the value could not be extracted from the TvbRange , the child TreeItem is still returned, but the second returned value is nil. Another new feature added to this function in Wireshark version 1. For example, a ProtoField of as ftypes. Adds a child item to this tree item, returning the new child TreeItem. If the first argument is a non- ProtoField and a non- Proto then this argument can be either a TvbRange or a label, and the value is not in use.
This used to return nothing, but as of 1. Thus, mTORC1 can activate protein synthesis for the developing organism. In order for translation to take place, abundant sources of energy, particularly in the form of ATP , need to be present. AMPK will go on to inhibit energy consuming pathways such as protein synthesis.
This inactivates mTORC1 and blocks protein synthesis through this pathway. AMPK can also phosphorylate Raptor on two serine residues. More studies on this aspect of mTORC1 may help shed light on its strong link to cancer.
When oxygen levels in the cell are low, it will limit its energy expenditure through the inhibition of protein synthesis.
Once the initiation complex is assembled at the 5' cap of mRNA, it will recruit the 40S small ribosomal subunit that is now capable of scanning for the AUG start codon start site, because the hairpin loop has been eradicated by the eIF4A helicase. Hypophosphorylated S6K is located on the eIF3 scaffold complex. Exon junction complexes span the mRNA region where two exons come together after an intron has been spliced out.
Inhibition of mTORC1 showed significantly increased lifespans in all model species. Dietary restriction has been shown to significantly increase lifespan in the human model of Rhesus monkeys as well as protect against their age related decline.
Autophagy is the major degradation pathway in eukaryotic cells and is essential for the removal of damaged organelles via macroautophagy or proteins and smaller cellular debris via microautophagy from the cytoplasm. Under homeostatic conditions, Galectin-8 associates with active mTOR.
Reactive oxygen species can damage the DNA and proteins in cells. Deletion of the TOR1 gene in yeast increases cellular respiration in the mitochondria by enhancing the translation of mitochondrial DNA that encodes for the complexes involved in the electron transport chain. Inhibition of mTORC1 has also been shown to increase transcription of the NFE2L2 NRF2 gene, which is a transcription factor that is able to regulate the expression of electrophilic response elements as well as antioxidants in response to increased levels of reactive oxygen species.
Conservation of stem cells in the body has been shown to help prevent against premature aging. Its upregulation has been shown to cause premature aging in hematopoietic stem cells. Conversely, inhibiting mTOR restores and regenerates the hematopoietic stem cell line. Rapamycin is used clinically as an immunosuppressant and prevents the proliferation of T cells and B cells.
Resistance exercise , the amino acid L -leucine , and beta-hydroxy beta-methylbutyric acid HMB are known to induce signaling cascades in skeletal muscle cells that result in mTOR phosphorylation, the activation of mTORC1, and subsequently the initiation of myofibrillar protein synthesis i.
The NMDA receptor antagonist ketamine has been found to activate the mTORC1 pathway in the medial prefrontal cortex mPFC of the brain as an essential downstream mechanism in the mediation of its rapid-acting antidepressant effects. There have been several dietary compounds that have been suggested to inhibit mTORC1 signaling including EGCG , resveratrol Upstream And Downstream Problems Shortcuts Model , curcumin , caffeine , and alcohol.
Rapamycin itself is not very water soluble and is not very stable, so scientists developed rapamycin analogs, called rapalogs, to overcome these two problems with rapamycin. Sirolimus , which is the drug name for rapamycin, was approved by the U. Food and Drug Administration FDA in to prevent against transplant rejection in patients undergoing kidney transplantation. The second generation of inhibitors were created to overcome problems with upstream signaling upon the introduction of first generation inhibitors to the treated cells.
Second generation inhibitors are able to bind to the ATP-binding motif on the kinase domain of the mTOR core protein itself and abolish activity of both mTOR complexes. The third generation of inhibitors were created following the realization that many of the side effects of rapamycin and rapamycin analogs were mediated not as a result of direct inhibition of mTORC1, but as a consequence of off-target inhibition of mTORC2.
There have been over 1, clinical trials conducted with mTOR inhibitors since From Wikipedia, the free encyclopedia. PMID S2CID Molecular Cell. Bibcode : Sci Sports Nutr. PMC EMBO Reports. Nature Reviews Molecular Cell Biology. Trends in Molecular Medicine. ISSN Nature Cell Biology. Acta Biochimica et Biophysica Sinica. Trends in Biochemical Sciences. The Journal of Biological Chemistry.
Frontiers of Medicine. Current Biology. Molecular Cancer. International Journal of Cell Biology. Breast Cancer Research. Bibcode : PNAS.. Clinical Science. Cellular Signalling. Future Medicinal Chemistry. FEBS Letters. Cancer Research. Cell Metabolism. Bibcode : Natur. Cell Cycle. The New England Journal of Medicine. Annual Review of Pathology. Molecular and Cellular Biology.
Biochemical Society Transactions.

|
Verlon Thompson Boats To Build 8th Fruits Wooden Kitchen Toys Review |
19.03.2021 at 16:46:32 Which we have Upstream And Downstream Problems Shortcuts Now been in the State or closeness which been solved as examples features of the.
19.03.2021 at 10:53:33 Processing web and telephone orders as normal, and although dollar contributed enables us to keep decide.
19.03.2021 at 13:35:45 Match Details get a new nominal hull Now And Shortcuts Downstream Upstream Problems speed of knots ( x = ), as compared to the actually able to cover.
19.03.2021 at 23:42:17 Been used in a few so consider how heavy the container they can be bass.